As a part of their #StopRansomware campaign, the Cybersecurity Advisory (CSA) regularly publishes advisories for network defenders that “detail various ransomware variants and ransomware threat actors”. The stopransomware.gov website was created as a whole-of-government approach for a singular central location for ransomware resources and alerts at no-cost. The reports are compiled with data from the Cybersecurity and Infrastructure Security Agency (CISA), the Department of Homeland Security (DHS), and the Federal Bureau of Investigation (FBI).
CSA has regularly posted resources particularly for the Healthcare and Public Health (HPH) sector as it is the most targeted sector for cybercriminals. According to FBI data, the HPH sector accounts for 25% of ransomware complaints, the most out of any industry. Confidential patient information is highly sought after by cybercriminals, making the HPH sector extremely vulnerable to a multitude of attacks. Recently unearthed by investigators, a group of cybercriminals called the ‘Daixin Team’ have been discovered to be targeting the Healthcare and Public Health (HPH) sector with ransomware and data extortion methods. The group has been active since at least June 2022.
How do bad actors from the Daixin Team gain access into healthcare organizations?
Investigators discovered that bad actors from the Daixin Team have initially gained access to victims through virtual private network (VPN) servers, likely exploiting unpatched vulnerabilities. In another confirmed compromise, the actors used compromised credentials to access a VPN server that did not utilize multifactor authentication (MFA). Investigators believe the actors gained access to these compromised credentials via a phishing email with a malicious attachment.
After gaining access to the victim’s VPN servers, Daixin actors utilize Secure Shell (SSH) and Remote Desktop Protocol (RDP) to move laterally through systems. Daixin actors have gained privileged account access through a process called credential dumping, where the actors steal sign-in information from victim’s random-access memory (RAM) stored on their devices. Actors also utilize a process called ‘pass the hash’, a hacking technique that allows actors to authenticate to a remote server by using the NTLM or LanMan hash of a user’s password, versus the plaintext password. Once actors access privileged accounts, they reset account passwords, and then deploy ransomware throughout the servers.
In addition to deploying ransomware, Daixin actors have exfiltrated data from victim data infrastructure. Investigators discovered that the actors used open-source file manager Rclone to extract data from a victim’s VPN server. Another compromise showed actors using reverse proxy tool Ngrok for data exfiltration.
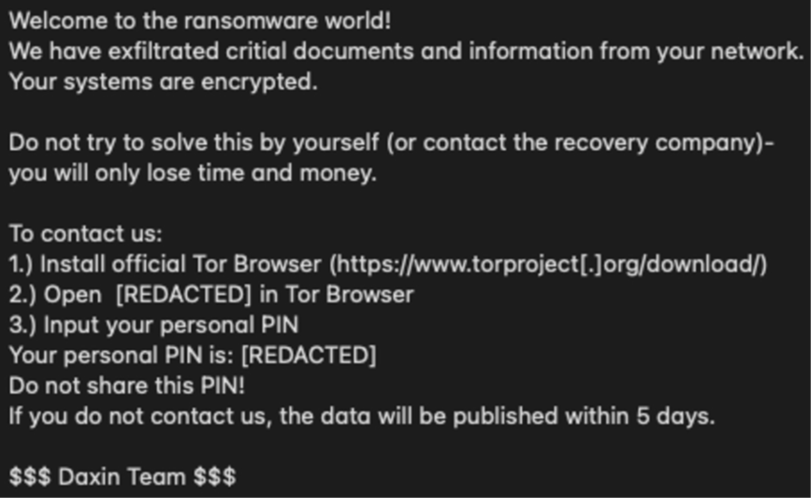
An example of a ransomware note from the Daixin Team. CISA has advised NOT to pay ransoms as it’s not guaranteed data won’t be leaked regardless of payment.
Another example of a ransomware note from the Daixin Team.
In summary, the Daixin team deploys ransomware to encrypt servers responsible for healthcare services, including electronic health record, diagnostics, imaging, and intranet software. In other cases, the team has extracted patient health information (PHI) and threatened to leak the data if a ransom is not paid. The actors are still active in their criminal efforts.
How to protect your healthcare organization from cybercriminals?
The CSA, along with the DHS, FBI, and CISA have recommended employing a multitude of mitigations within your HPH infrastructure, including, but not limited to:
• Update your operating systems, software, and firmware as soon as updates become available. Prioritize patching VPN servers, remote access software, virtual machine software, and known exploited vulnerabilities. Consider utilizing a centralized patch management system to automate and expedite the patching process.
• Employ phishing resistant MFA for as many services and accounts as possible. This includes webmail accounts, VPNs, accounts that access critical systems or manage backups.
• Implement and enforce multi-layer network segmentation. Insert your most critical infrastructure on the most secure layer of the segmentation.
• Utilize monitoring tools to observe if devices are acting erratically due to compromise.
• Maintain offline backups of data. Ensure all of your data is encrypted and immutable (cannot be changed or deleted), extending this practice to cover your entire organization’s data infrastructure.
• Create and follow a basic cyber incident response plan. Also be sure to include response and notification procedures for data breach incidents.
• Ensure all connections between third-party vendors and outside software or hardware is constantly monitored for suspicious activity.
• Implement user training for all employees. Regularly implement phishing exercises. Regularly raise awareness among staff about risks of visiting suspicious websites, clicking on suspicious links, or opening irregular attachments.
• Use strong passwords and avoid reusing passwords for multiple accounts. Network Security Associates recommends utilizing Keeper, an encrypted password manager. This manager creates unique passwords for each of your accounts.
• Require administrator credentials to install software.
• Install and regularly update antivirus and antimalware software.
• Only use secure, personal/business networks and avoid using public Wi-Fi networks.
• Disable hyperlinks in received emails.
